People distinguish three types of AS:
- Stub AS
- It is connected to only one other AS. For routing purposes it is treated as part of the parent AS.
- Multihomed AS
- It is connected to more than one other AS, but does not allow transit traffic. Internally generated traffic can be routed to any of the connected ASs. It is used in large corporate networks that have a number of Internet connections, but do not want to carry traffic for others.
- Transit AS
- It is connected to more than one other AS and it can be used to carry transit traffic between other AS's.
Here is a high-level view of the internet, from your workstation, up to the content providers such as yahoo and the New York Times.
Standards, Protocols, Layered Architectures
Standards and Protocols are used to define representation and interaction modes within a network and to make certain functions generally available. Standards and protocols usually come in groups that work well together and constitute protocol suites or protocol stacks. New standards and protocols are continuously being introduced. They fit within general frameworks called Architectures. Conceptually dominant among such architectures is one established by the International Standards Organization (ISO), which is called the Open Systems Interconnect (OSI). The OSI architecture is not a specific fixed set of protocols and standards, it is the definition of the functional layers of networks and of the protocols and standards that may be used. Of course, in practice, people tend to associate a network architecture with its most popular standards and protocols. Another network architecture that is not as general as the OSI architecture, but that introduced the most used protocols (and it is overwhelmingly the most used), is the TCP/IP Architecture.Both the the OSI and the TCP/IP architectures are layered architectures, that is the functionality of the network is decomposed into layers, where a higher level layer uses the services provided by the layer immediately below it and where across a network communicating entities communicate exclusively at the same layer (i.e. if a sender entity at layer i sends a packet P, the receiver entity at layer i will receive P; these two are called peer entities).
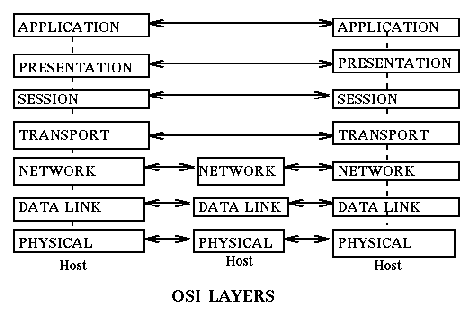
OSI Architecture
Stallings in his operating systems book [Prentice-Hall 1998] has the following brief characterization for the OSI Layers:- Physical (Layer 1):
- Concerned with transmission of unstructured bit stream over physical medium; deals with mechanical, electrical, functional, and procedural characteristics to access the physical medium.
- For example, RS-232, SONET [Synchronous Optical NETwork]
- Data Link (Layer 2):
- Provides for the reliable transfer of information across the physical link; sends blocks (frames) with the necessary synchronization, error control, and flow control. It uses physical addresses.
- For example, HDLC [High Level Data Link Control].
- Network (Layer 3):
- Provides upper layers with independence from the data transmission and switching technologies used to connect systems; responsible for establishing, maintaining, and terminating connections. Routing is carried out in this layer, selecting routes, and enforcing them. Addressing is at the logical level, with translation to the physical level.
- For example, IP [Internet Protocol] (connectionless), X.25 (connection oriented).
- Transport (Layer 4):
- Provides reliable, transparent transfer of data between end points; provides end-to-end error recovery and congestions and flow control.
- For example, TCP [Transmission Control Protocol] (connection oriented), UDP [User Datagram Protocol] (connectionless).
- Session (Layer 5):
- Provides the control structure for communication between applications; establishes, manages, and terminates sessions (consisting of one or more connections) between cooperating applications. It may deal with class-of-service (i.e. different quality of service - for example, data expedition, reduced jitter, ..)
- For example, RPC [Remote Procedure Call].
- Presentation (Layer 6):
- Provides independence to the application process from differences in data representation (syntax).
- For example, XDR [eXternal Data Representation].
- Application (Layer 7):
- Provides access to the OSI environment for users and also provides distributed information services.
- For example, telnet, ftp, finger.
application --> DNS SMTP FTP TELNET HTTP
| | | | |
| | | | |
| | | | |
| +--------------------------+
| |
| |
transport ----> UDP TCP
| |
| ICMP |
| | |
+------------------------------+
|
|
network ------> IP<--------------+
| |
ARP | |
| | |
+--------------+ |
| |
link ------> Ethernet PPP
| |
| |
physical ----> Ethernet modem
where:
As you can see from the diagram, there tend to be multiple protocols at each layer, except at the network layer. For this reason people talk of the hourglass structure of the internet protocols and see IP as the king of internet protocols.
There is a fundamental difference between the lowest three levels (the communication subnet) and the top four levels of the OS architecture. The bottom layers are between directly connected hosts thus they involve all the hosts in a path from sender to receiver. The top four layers are end-to-end protocols, that is, the communication is stated in terms of only the original sender and the final destination, independent of how many intermediate hosts are traversed. Intermediate nodes do not participate at all in the processing of the higher level protocols, to them it is data. [Think in terms of overhead: In the source and target node protocols at all layers are processed. In the intermediate nodes only protocols in the bottom three layers are processed.] This has a direct impact on efficiency: for example, error checking in protocols at the higher level is only done at the sender and receiver, not at each intermediate hosts.
Three related concepts in discussing layers are Services,
Interfaces, and Protocols.
Services are what a layer
provides to the layer above it (the former is the Service Provider
and the latter is the Service User).
A layer may provide more than one service. For
example the transport layer provides a connection-oriented service and a
connectionless service. A service will have a "service model"
expressed as a set of
primitives used to access that service. There are four basic
kinds of primitives:
- Request: A requesting entity asks for a service.
- Indication: A responding entity receives a request for service.
- Response: A responding entity responds to a request.
- Confirm: A requesting entity receives a response to a prior request.
Interfaces are the set of rules that govern the interactions of entities at layer i+1 and i in a node. When an entity at layer i+1 in a node wants to send an SDU to an entity at layer i+1 in another node it creates an Interface Data Unit(IDU) that will be passed to the layer i in the origin node. The IDU will consist of the SDU plus some control information, for example the length of the SDU.
Finally a protocol is a specification of how information is actually transfered at a layer from a sender to a receiver. A protocol will pack the data into Protocol Data Units (PDU). It is possible that a SDU passed from layer i+1 to layer i will be sent to receiver fragmented into a number of PDUs.
Each message (message is the preferred name for the PDU at the session layer and above; at the transport layer segment is preferred; at the network layer datagram and packet are used; at the data link, frame is used; and at the physical layer packet is common) consists of data being transmitted plus information required by the protocol for addressing, error detection, etc. This extra information appears as a header before that data and (may be) a trailer after the data, i.e. the data is encapsulated in the message. [Not all messages have both a header and a trailer. Usually the trailer is not present.] The message sent at layer i will be transmitted as data by the layer below it. Assuming that the layer below can transmit this data as a single message we will have the situation
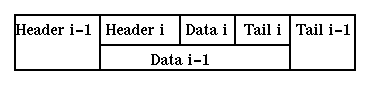
Note that the headers and tails constitute transmission overhead, reducing the utilization of the bandwidth of the communication channel. Of course this is only part of the communication overhead: retransmissions and acknowledgements further reduce bandwidth.
A concept often used in communication is session. It consists of one or more connections. For example, a program on machine A may be involved in communication with a program on machine B, the connection drops due to communication problems. When communication is reestablished the programs continue from where they were in the session using a new connection. An example of a session is the interactions during a remote procedure call. The requestor has to send the request, possibly in multiple messages, the receiver collects them, processes the request, then sends back the results. All in one session.
The transmission units at different layers may be of different maximum sizes. We have here the same distinction that exists between "logical" and "physical" records in file systems.
A number of issues should be kept in mind when we analyze a protocol and its implementation. Among them:
- Framing: How do we recognize the beginning and end of a message (or packet, or frame, or ..);
- Flow Control: How do we make sure we don't send too much information to the receiver so that it cannot handle it and has to "drop it on the floor"; it is normally managed by the receiver that informs the sender about how much data it is ready to accept;
- Congestion Control: How do we make sure that we don't have too many messages trying to get into a communication channel. Thus causing delays and perhaps lost packets; it is normally managed by the sender, and possibly by the routers;
- Multiplexing: How a single communication channel can be shared for more than one conversation;
- Addressing: How do interlocutors address each other [host interfaces are known by their IP address (a 32 bit integer); unfortunately in ethernet the address understood by the hardware is the Ethernet address (a 48 bit integer) of the connector; thus there is need of a way to translate from IP to Ethernet addresses. In general, this requires an address resolution protocol (ARP is such a protocol).
- Error Detection and Correction: what we do to detect if an error has occurred in transmission and how to correct it (recover from it).
-
Fragmentation: One message at a layer may have
to be fragmented over multiple messages at a lower layer.
A layer may be able to accept messages of length
N, but the implementation of the layer in terms of a protocol at the layer
below may accept only messages of length M, with M < N. Thus the original
layer must be able to fragment the original message into a number of messages
at the lower level. These fragment may then be sent across different routes
and the receiver will have to worry about missing fragments, incorrect
received order, in recombining them into the correct received message.
This problem occurs in particular between the network layer (IP protocol)
and the data link layer, where the IP packet needs to be split into a number
of fragments. Maximum Segment Size (MSS) is the minimum maximum size of
the segments used at different layers in a connection (so if at a layer
the maximum segment is 4096 bytes and at another it is 1500,
then the MSS is 1500).
The opposite situation may also occur: At the data link layer with Ethernet we have messages of up to 1500 (+26 of overhead) bytes. At the network layer we may have a limit of 128 bytes. [Or the data link unit may be 53 bytes...]
As we need to worry about the maximum sizes in different layers, we need also to worry about the different maximum sizes allowed by the different links that messages will traverse. So one may talk of a path maximum size. If we send packets of at most that size, they will not be fragmented on the way.
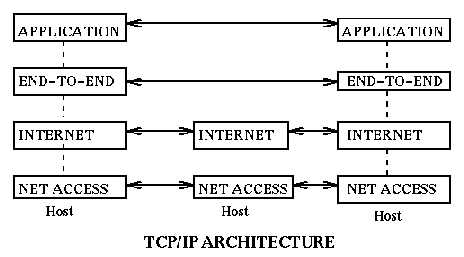
TCP/IP Architecture
The TCP/IP architecture was developed mainly in the US. It is the one that has the largest number of users. It represents pragmatic solutions to problems as they arose. It involves only five layers: The application layer (same as in OSI), the end-to-end layer[also called transport layer] (TCP or UDP or ...), the internet layer (IP, or ICMP, or ..), the net access layer [also called the network interface layer] (Ethernet, or ATM, or PPP, or SLIP, or ....), and the physical layer.